
Sports ISAC
Securing the Future of Global Sports
Discover the Advantages
The definitive intelligence community for professional leagues, venues, and sports technology partners. We share threats. We build resilience. We protect the integrity of the game.
Actionable Threat Intelligence
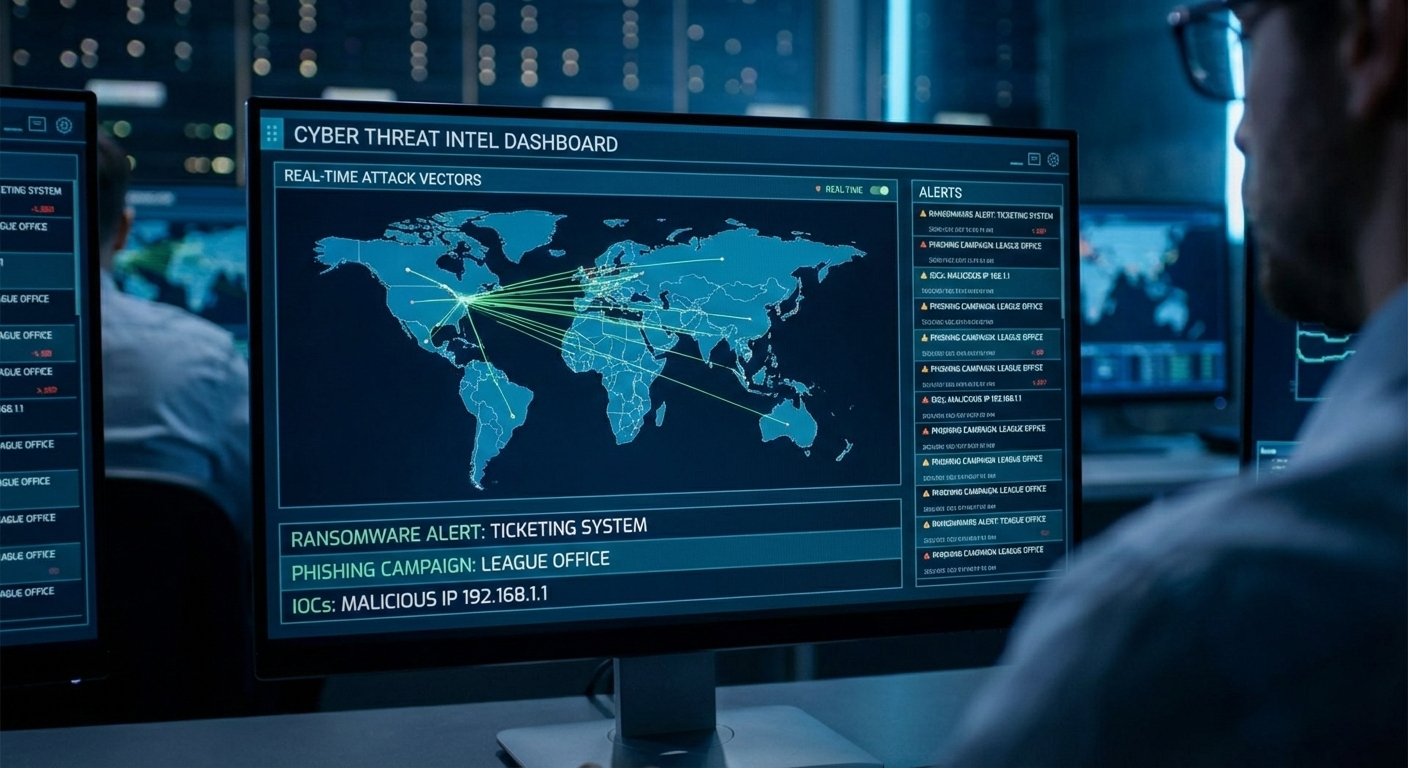
Real-Time Alerts: Immediate notifications about active ransomware campaigns, zero-day vulnerabilities, or physical security threats.
Enriched Data Feeds: Automated feeds (often using the STIX/TAXII protocol) that allow members to plug threat data—such as malicious IP addresses or file hashes—directly into their firewall or security software.
Deep-Dive Analysis: Reports that break down the Tactics, Techniques, and Procedures (TTPs) used by threat actors specifically targeting that industry.
Vulnerability Notifications: Proactive alerts when a member’s specific public-facing assets (like a website or server) have an unpatched weakness.
Secure Collaboration & Networking

ISACs create a “safe space” where competitors can cooperate on security without fear of sensitive data leaking to the public or regulators.
Secure Portals & Chat: Private forums where security teams can ask, “Is anyone else seeing this weird traffic?” and get answers from peers in minutes.
Anonymized Sharing: A mechanism for members to report a breach or a “near miss” without their company name being attached to the report.
Working Groups: Sub-committees focused on specific issues, such as Cloud Security, Fraud Prevention, or Drone Mitigation.
Resilience & Incident Response

Tabletop Exercises (TTXs): Large-scale simulations where members practice responding to a sector-wide crisis (e.g., a massive ticketing system failure or a regional power outage).
Incident Response: During a major event, the ISAC can act as a bridge to government agencies (like the FBI or CISA).
Best Practice Playbooks: Standardized “how-to” guides for handling common industry threats, helping smaller members reach the same security maturity as larger ones.
Community Discussions
In a Sports-ISAC, the discussions are far more than just “chatting about security.” They are high-stakes, real-time exchanges where a vulnerability found by a team might save another team from the same attack that afternoon.
The value of an ISAC lies in its Traffic Light Protocol (TLP), where members share sensitive details—anonymously if needed—that they would never tell the press or even their fans.
Cybersecurity & Data Privacy
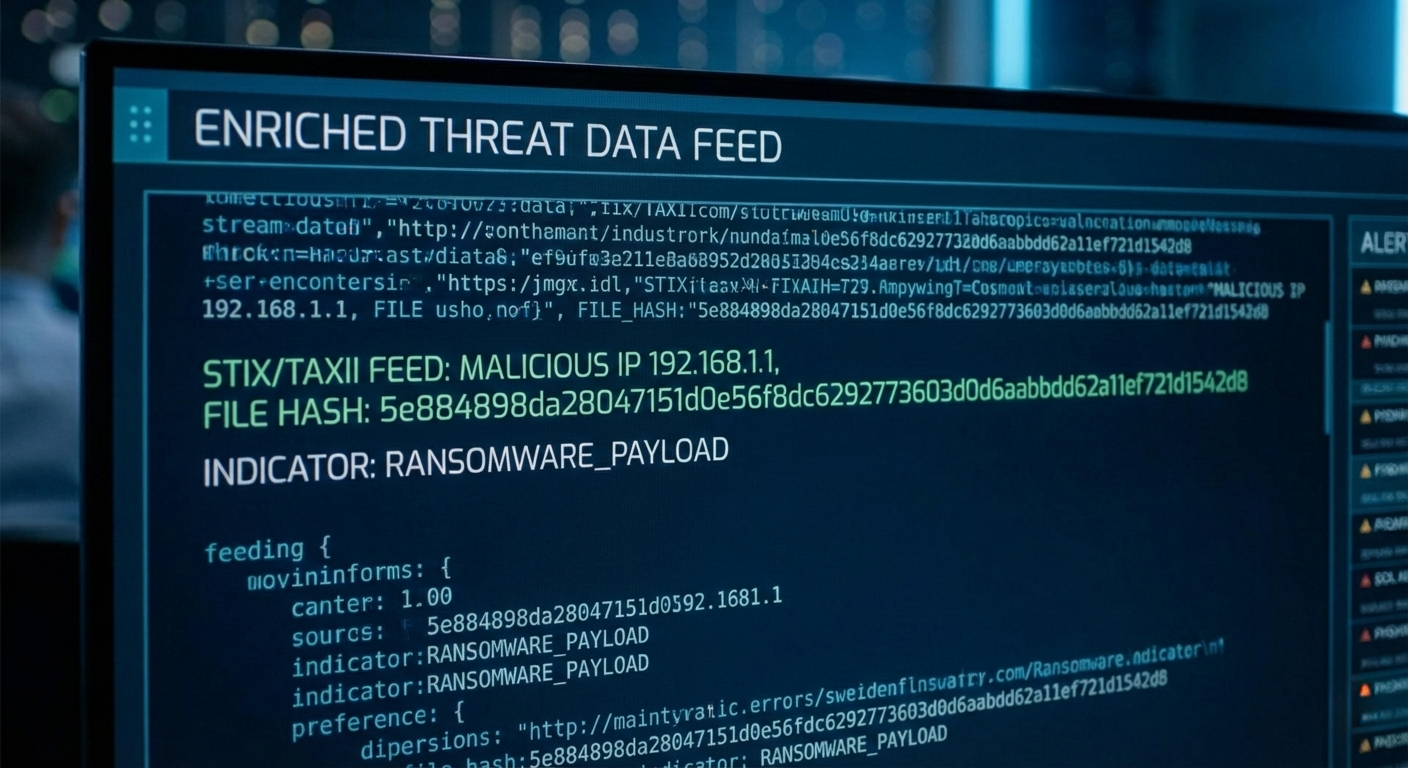
Since sports organizations handle high-value player data and massive amounts of fan credit card info, cyber-discussions are constant.
Player “Scouting” Hacking: Discussing attempts by rival entities (domestic or foreign) to access proprietary draft boards, player health biometrics, or trade negotiation emails.
Ticketing Ransomware: Sharing “Indicators of Compromise” (IOCs) from a new ransomware strain that specifically targets stadium turnstile systems or digital ticketing apps during game day.
VIP Phishing: Warning peers about a specific spear-phishing campaign targeting Team Owners or General Managers via “urgent” league-office spoofed emails.
Physical & Venue Security

This is where stadium operators and local law enforcement collaborate to protect tens of thousands of people in one location.
Rogue Drone Mitigation: Real-time alerts about unauthorized drones over stadiums and discussing which “jamming” or detection technologies are legal and effective.
Crowd Dynamics & “Field Storming”: Analyzing footage or data from recent incidents (like a “court storming” or a stampede at a gate) to develop better physical barriers or de-escalation tactics.
Severe Weather Protocols: Sharing “Trigger Points” for when to evacuate a stadium for lightning or extreme heat, including how to handle the “shelter-in-place” logistics for 60,000 people.
Game Integrity & Betting Fraud
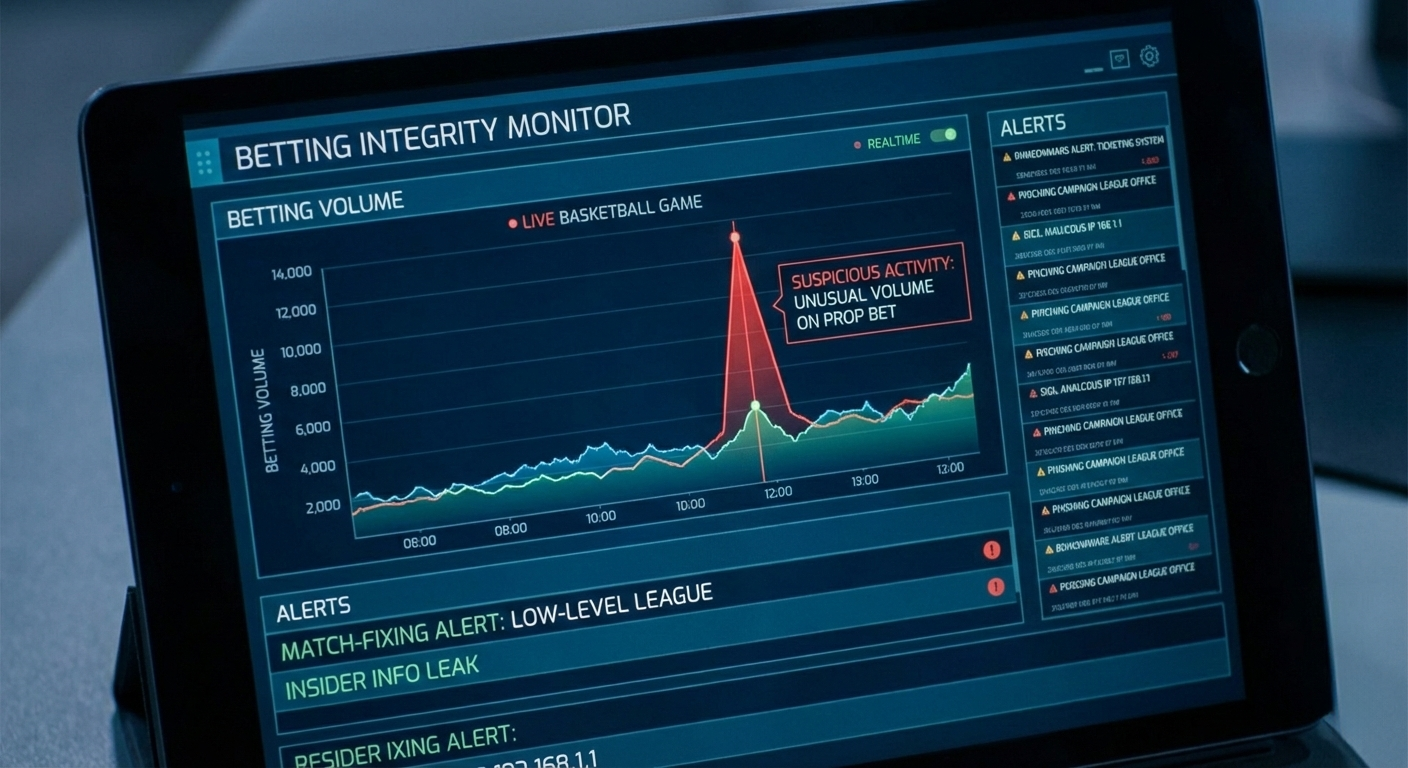
With the explosion of legalized sports betting, protecting the “purity” of the game is now a security function.
Suspicious Betting Alerts: Sharing data from monitoring services about “irregular volume” on a low-level minor league game or a specific prop bet that might indicate match-fixing.
Inside Information Leaks: Discussing ways to secure the “locker room perimeter” so that injury news doesn’t leak to gambling syndicates before the official report.
Anti-Doping Intel: Discussing new “gray market” supplements or methods being used by athletes to circumvent standard testing.
Operational & Legal Challenges

ISACs also act as a policy brain trust for the industry.
AI in Surveillance: Discussing the legal and PR risks of using facial recognition for “fan blacklists” or frictionless entry.
Staffing Shortages: Benchmarking how other venues are handling the shortage of trained security guards and whether “autonomous security robots” or AI-monitored CCTV is a viable fix.
Third-Party Vendor Risk: Reviewing the security posture of shared vendors, such as the companies that provide the “In-Game App” or the stadium’s Wi-Fi infrastructure.

“On the field, we are rivals. In the security operations center, we are one team. The Sports-ISAC allows us to share ‘scouting reports’ on our real adversaries—the cyber and physical threats that don’t care about the score or the standings. We defend the game together.”
Join Sports ISAC
Elevate your organization’s security posture by joining a global community of specialists dedicated to protecting the integrity of sports. As a member of the Sports-ISAC, you transition from isolated defense to a unified front, gaining exclusive access to real-time threat intelligence, industry-specific playbooks, and a secure network of elite peers. Whether you represent a professional league, a global venue, or a sports technology innovator, your participation strengthens the entire ecosystem against cyber, physical, and integrity-based threats.
Protect the game. Protect the fans. Secure the future.
